The demand for user-friendly, secure mobile applications has never been higher. Few of us can imagine having to go back to a life where the information we want, at any given moment, isn’t available at our fingertips through our smartphones and mobile applications. Consumers look to enterprises to create mobile applications that provide tools and information organized in a way that is intuitive, easy to use and compatible with their on-the-go lifestyles.
AI has presented enterprises with the opportunity and ability to create innovative mobile application software more quickly and efficiently, but with this increased speed comes a new series of risks that cannot be ignored.
According to a 2023 Gartner report, GenAI can save developers 20-50% of time spent on repetitive coding tasks. In addition, Google’s 2023 Accelerate State of DevOps Report found that teams with faster code reviews have 50% higher software delivery performance and those with teams with generative cultures have 30% higher organizational performance. That’s why, according to GitLab, 92% of programmers are already using AI-powered coding tools – to help orchestrate the coding process, automate resolutions to gain a competitive advantage, and reduce the complexity of software development and delivery. The challenge for large enterprises that want to execute more modern software delivery is that AI has the potential to throw the ability to scale into total disarray.
As a result, and seemingly overnight, the work coming out of DevSecOps is gaining prominence at the highest levels of business decision-making, as more companies try to get their arms around AI adoption and incorporate into their broad business strategy planning. The risks associated with code developed from unknown sources is not well understood. Additionally, the patchwork of individual AI usage versus official corporate AI usage exposes businesses to a higher level of risk.
At the developer level, a lack of trust or confidence in the security of their code is inexcusable; DevSecOps must lead the AI-security strategy for the enterprise. Because nowhere is this need for guardrails more abundantly clear than in app development environments. Once an application leaves the relative safety of the corporate firewall and reaches the hands of a consumer, particularly from a mobile device, it is in ‘the wild’ – an unprotected, and uncontrolled environment.
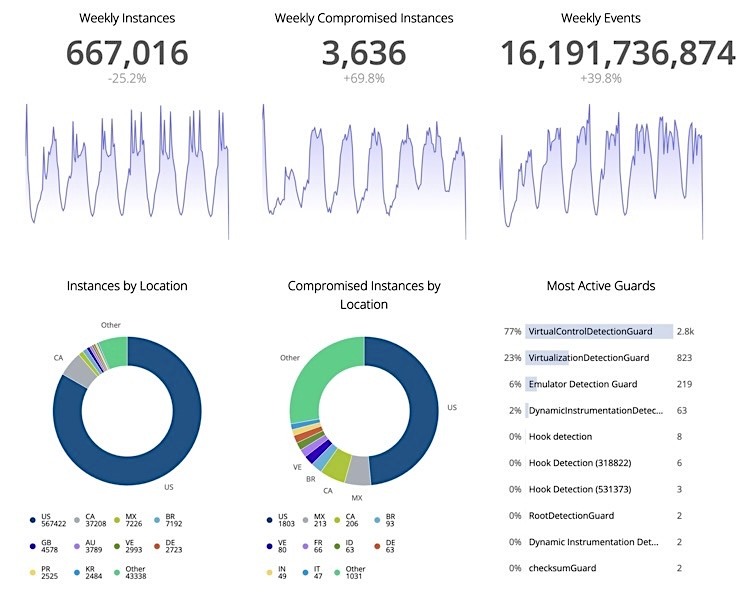
Consider Digital.ai’s 2023 Application Security Threat Report that shows 57% of all applications in the wild are “under attack.”. Another recent report revealed that about 84% of analyzed applications had not deployed any form of “repackaging” detection, a commonly used technique by threat actors to modify existing code. This widens the possibility for theft of sensitive user information.
Dodge these mobile app development mistakes
Historically, security has often been short-changed and excluded in the DevOps process; it has been seen as an impediment that slows down innovation without an obvious starting and end point, but enterprises and developers alike are becoming privy to its necessity.
There are a few major and commonly made mistakes that can lead to significant vulnerabilities in the delivery of mobile applications. With proper security guardrails in place during the development process and a continuous testing model implemented before deployment, these mishaps can be avoided.
- Postponing security integration: One of the most significant mistakes in mobile app development is the belief that security can be added after the app is ready for deployment. This oversight can lead to the omission of essential security measures, potentially causing bottlenecks in workflow and frustrating both developers and testers. It’s crucial to incorporate security measures throughout the entire app lifecycle to mitigate the risk of vulnerabilities.
- Misconceptions about security expertise: Another common error is the assumption that developers need advanced knowledge in information security or coding techniques to enhance security. Many security controls, such as anti-tampering and code obfuscation, can be applied to code after the development phase but before the testing phase, ensuring a more secure app without requiring specialized expertise and in a fashion that does not impact the normal development workflow.
- Lack of comprehensive testing solutions: A critical mistake made by software development teams is neglecting to implement a robust and continuous testing solution. These solutions, acting as device farms, allow thorough testing in a wide range of environments. They are essential for identifying potential vulnerabilities and ensuring the app’s functionality and security in various conditions, reducing burden on the development team and seamlessly integrating into post-build environments and release orchestration workflows.
Ultimately, enterprises should never settle for “good-enough” protection across the board. That mentality will come back to bite as the pace of AI-augmented application development becomes increasingly attached to compliance and governance concerns.
Fire Up Your Growth!
Moburst propelled leading brands like Google, Reddit, and Uber to the next level. Let’s ignite your Success journey today!
Claim Your FREE Growth Fuel!To help ensure that more releases reflect better quality software, development teams need to determine the risk of each application, each software update, feature and function, and then protect each one commensurate with that risk value. Releasing software quickly and efficiently is never a win if what is being released is insecure and vulnerable to threat actors.
Enterprises beware: the consequences of neglecting security during mobile app dev
Threats associated with mobile applications are especially tricky, often difficult to pinpoint for developers since the attack surface spans the entire SDLC.
These security risks can have serious consequences in any industry, yet the stakes are even higher when it comes to healthcare and financial applications. For example, breaches of highly sensitive personal banking and medical information opens the door to massive financial and legal ramifications, even nuclear verdicts that can lead to irreversible damage.
In healthcare, increasingly more mobile apps are responsible for monitoring vitals like blood sugar levels and tampering with this type of data could even be life threatening. We have yet to publicly see this scenario play out, but hospitals are under attack seemingly all the time, with around half of all U.S. hospitals being targeted with ransomware. Recent data from Check Point Research finds healthcare organizations experienced a 60% increase in cyber-attacks in 2022, or 1,426 attacks per week.
The weapon becomes the tool: AI’s role in app protection
The news about AI is not all negative – when used appropriately, it is a powerful security tool for the business. It should not be feared or kept out of the organization.
Already, according to Forbes Advisor, 51% of businesses are utilizing AI in cybersecurity and fraud management. The technology is useful in identifying unknown threats, managing, and analyzing risk of change through change risk prediction functionalities, and accelerating detection and response to risks, but enterprises should stop reacting to inconsistencies, and instead accelerate towards a solution.
As we navigate toward the future, AI will continue to accelerate the pace of measure and countermeasure development. Building secure software is not a “nice to have” – it is a must-have, which is what makes predictive AI-tools necessary to stay ahead of emerging threats. Security-minded developers who apply AI intelligently throughout the entire SDLC will be able to do more and faster than their counterparts who are not using AI-augmented tools.
Prioritizing security proportional to risk is a non-negotiable principle and AI’s role is pivotal. Embracing AI as a strategic ally in app development, delivery and protection is the hallmark of the future.
Learn more about unlocking the power of AI during the entire software delivery lifecycle here.