As more people use apps on their mobile devices, cybercriminals continue to develop new methods to exploit app vulnerabilities. In 2022 cyberattacks rose 38% over the previous year and the number of new mobile malware variants was up 54% in 2019. Promon, the application shielding technology, recently tested 357 high-earning Android mobile games to reverse engineer or manipulate apps. Shockingly, 81% (289) of the apps showed zero defence against these attacks and couldn’t detect a compromised device.
Defenceless apps
In Promon’s four-step examination, one of the tests involved “repackaging,” a technique used by malicious actors to modify the existing source code of mobile applications. With this technique, hackers can insert their own code on top of an app’s source code and perform additional background tasks outside of the app’s intended functions.
This opens the door for cybercriminals to steal user login credentials via a tactic called credential stuffing.
Astonishingly, the tests revealed that a whopping 84% of apps lacked the capability to detect if their source code had been injected with harmful code, leaving them vulnerable to a host of cyberattacks.
Only 15.7% (56) of apps had deployed any form of repackaging detection, making them the exception rather than the rule.
🚀 Grow Your App! Free ASO Audit by Award-Winning Agency
Discover how Yodel Mobile, the App Marketing Agency of the Year, can transform your app. Gain insights with our free ASO audit, proven in elevating apps like B&Q, Afterpay and Gymshark. 🌟
Get StartedThe company also assessed app vulnerabilities related to hooking frameworks which are utilized to monitor, modify, and redirect events in a mobile application.
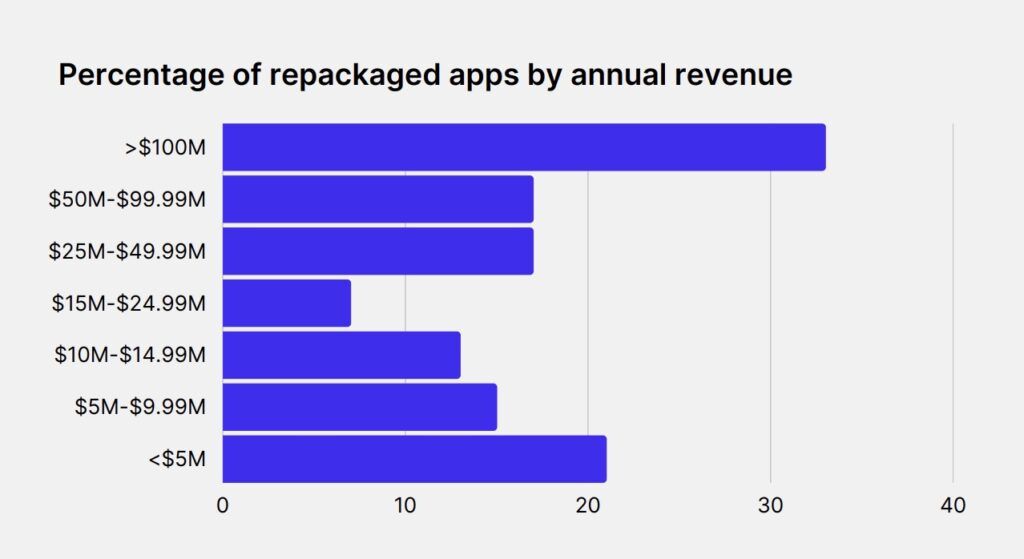
Promon’s tests repackaged almost 85% of all the apps tested
Source: Promon
Serious developers and security experts use them to identify vulnerabilities and malicious activities. However, they can also be used for malevolent purposes like stealing sensitive data.
Only 5-8% of the apps tested could protect against attacks through frameworks.
Finally, only one app could detect the presence of a rooted device, leaving the vast majority unprotected and susceptible to a host of security breaches.
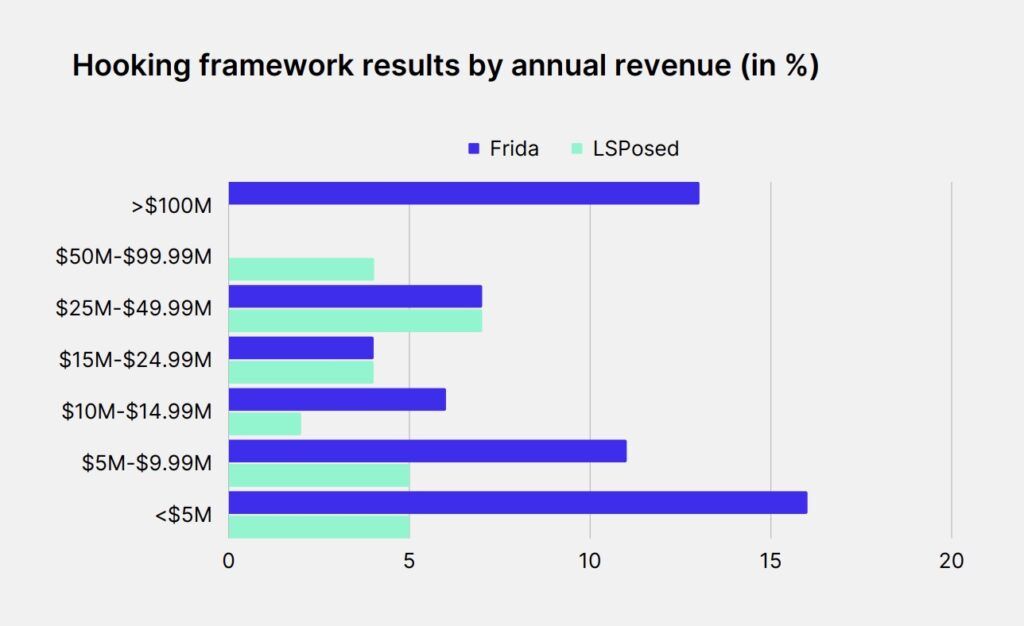
13% of apps with $100M or more in annual revenue could detect hooking framework Frida, although none could detect LSposed.
Source: Promon
Why developers must address cyberattacks
Gaming-related cybercrime can be catastrophic for developers and publishers. Where games fail to provide a safe and secure experience, consumer trust declines and developers ultimately make fewer sales and see their downloads dwindle.
“We were surprised at how many mobile games had a gap in cyber protection. From a technical standpoint, these aren’t complex attacks,” says Benjamin Adolphi, head of security research at Promon.
“These are basic tools and techniques leveraged by cybercriminals every day, and protecting against them should be a priority for developers when building these apps. While attracting millions of players, mobile gaming companies should consider bridging the gap between mobile app protection and ensuring that all gamers enjoy the game. Doing that will not only protect the game experience, but ensure that gaming companies defend their brands and grow their revenue.”
Tools like hooking can modify game code and give players an unfair advantage, causing developers to lose revenue as players may opt-out of in-game purchases.
Worse still, hooking frameworks can be utilized to extract sensitive data like proprietary game code, user data, or cryptographic keys, exposing developers to security risks and IP theft. If games are known to be vulnerable, they risk losing their reputation and player trust, causing lasting damage to the developer’s bottom line.
Key takeaways
- 81% of apps tested showed zero defence against cyberattacks
- 84% of apps lacked the capability to detect if their source code had been injected with harmful code
- Only 15.7% of apps had deployed any form of repackaging detection